Organizations and Tools to Help
What happens if you have a relationship with someone that sours, and the former partner posts private photos online? Or if a cyber actor gains access to your phone or hard drive and steals private photos for blackmail? Or, for the actors in the audience, if an obsessed fan takes production or press photos of you and photoshops them onto a more lurid image?
In many cases, the answer seems to depend on what country you’re in, or which state you reside within the US, as we have separate state and federal jurisdictions.
Helpful Organizations
The Cyber Civil Rights Initiative is the US’s leading non-profit 501(c)3 organization to assist people faced with this harrowing situation. It formed in 2013, stemming from how one woman’s case showed a need for such a grassroots effort to address these issues. Another organization, Without My Consent, started in 2011 but ended in 2019, when it became a project under CCRI. The CCRI maintains the WMC websites of resources and tools to assist people with removing non-consent images.
In the UK, the SWGfl (South West Grid for learning) is charity that has held safe internet as a goal “for the last two decades”. (The website registered in 2000.) They manage the Revenge Porn Hotline which has recently created a tool on Stop NCII which is available for anyone to use.
End Cyber Abuse is a global collective founded in 2018. They focus on bringing awareness, advocating for better policies, and building survivor support.
Each of these sites cross-link and offer more links to international resources.
Removing Images from Social Media
If someone’s image has already been shared, the best recourse is to go to the social media platform itself. Stop NCII’s list is comprehensive, and I recommend it.
The StopNCII.org site includes a powerful tool that will help someone post removal requests of unethically-shared private images without having to share the image further.
On the site, you can select up to 20 source photos. The tool creates a hash of the images, and only sends this hash to social media outlets. These outlets who have made partner agreements with SWGfl will scan their platforms for the matching hash, and if they find a match, they remove it.
The StopNCII site explains that they cannot check for altered photos yet. I’ve reached out to see if they’re working on a solution for this, and I will update this if so.
Hashing
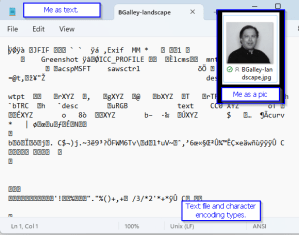
They can do this because, at the end of the day, anything we send by computer is broken down to MANY ones and zeroes. You don’t send an actual image. You send a piece of gobbledygook (like my photo on the right, as seen in Notepad) that tells the other computer, “Hey. This is an image. It’s 640 x 480. At position (0,0), the color is light gray…” My dark brown / black hair doesn’t start until like (4,230). (PS: Not all photos start (0,0) at top left.)
PS: Altering is tough, because it changes the hash. If we chopped off the bit above my hair, or the left third of my image, then (0,0) isn’t light gray, but dark brown. Ditto if we applied a color filter or changed the resolution.
Characters are also assigned numerical values too via “character set encoding”. It’s not really a = 1, b = 2, c = 3 – but you can picture the idea. Because again, we have to get down to ones and zeroes, and numbers can be expressed as ones and zeroes really easily.
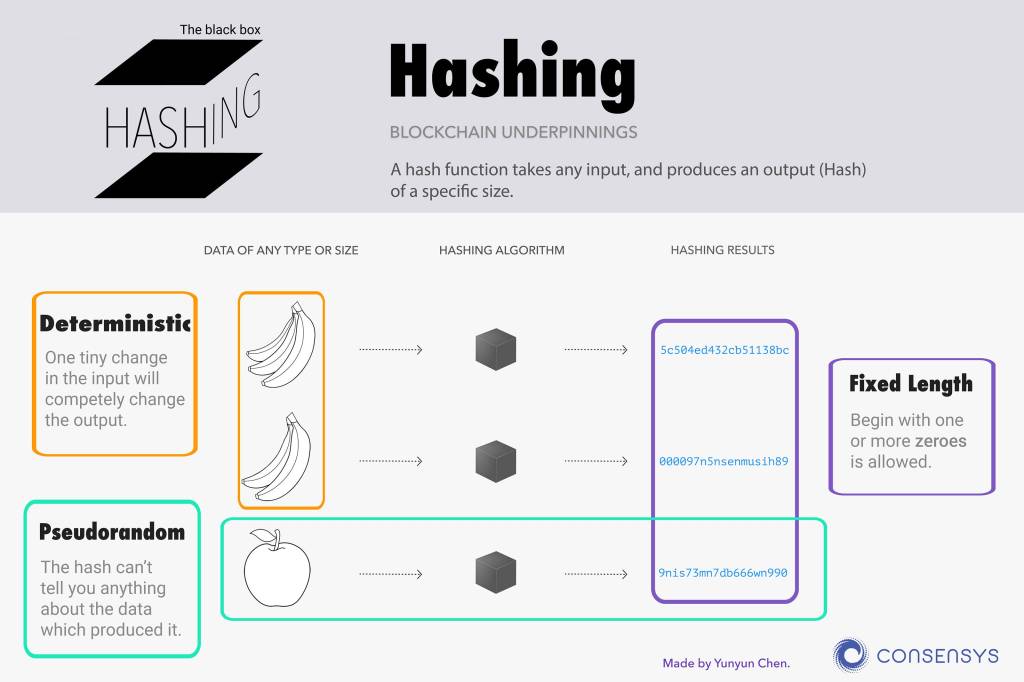
Because it can be expressed as text, we can put it through a hashing algorithm, which is a fancy way of saying it will dice the file up into a certain number of pieces, all the same size. It then performs an operation that results in a number, and then we use the character set to match that number with a character again. (“Group 1 was abc. 1 + 2 + 3 = 6, which is ‘f.’ Thus, the hash of group 1 is ‘f’.)
Just like dicing up a food, you can’t put a hash back together again. “6” could be “abc, cba, bac” or even “aad, daa, bbb”.
I like how Consensys make this concept into a picture, even they’re using it to explain blockchain. Clicking the image will take you to their source page.
We also use hashing in email. Your email provider hashes the email body before you send it and includes it as a header property. The email provider who receives it hashes the email again. If they match, “Yay! No tampering!” (This protocol is called DKIM. If your company isn’t using it, ask them to.)

You must be logged in to post a comment.