Anatomy of a Phishing Attack VIII
In recent years, the US has taken a more diligent view on China and its Made in China 2025 initiative, which aims to increase China’s market share into higher-valued product chains. China’s strategy isn’t just in growth and development, but by any means necessary. The FBI created a video “Made in Beijing” detailing various efforts reaching back to 2010. Bloomberg posted an article about a separate case about GE business and state secrets. And on Wednesday, 8/23/2023, KnowBe4 published an article looking at how a Chinese spy created fake LinkedIn profiles and companies to target UK officials.
What’s all this have to do with me? I received an invite today (8/25) that I think fits the fake account profile.
The Bait
I’m still jobhunting, and I have received several legitimate invitations and requests for networking by potential recruiters and staffing agencies. This provides an opening for cyber actors, at I currently expect email or messages from unknown parties that might entertain job offers. And really, there’s nothing in this initial invitation that screams “red flag” under that premise.

The Hook
I’m going to lean on LinkedIn’s article here, as I didn’t engage with Mister E. (Heh, “mister eee”, “mystery”) The MO they saw was the cyber actor, posing as the CEO, would schmooze his marks and lure them to him in order to get state secrets. Okay, I don’t fit that profile.
But the hook is still likely a (fake) job offer.
The Reel
In my case, it’s more likely that they’d want to bring legitimacy to their webpage by being able to link a real person (me) to it, and along the way, they’d likely try to trick me into purchasing my own work supplies.
The Catch
LinkedIn’s basic reporting feature (found off the … menu of each post and message) doesn’t have a place to offer details. All their safety and security team has to go on is the content of the message itself. That would have likely come up with a “we don’t see anything wrong”, so I followed up by going to their Help Center and opening a case. There, I was able to link the account and company URLs, give details of what I found, and include the screenshots you see within this post.
I also sent a report to the FBI’s IC3 site.
Anatomy of the Attack
As I mentioned above, the invitation itself doesn’t have much to call it out. I am seeking a job, so while I didn’t expect this invite, I am expecting recruiters to notice my profile and send invites. The invite pretexts expectations – by calling Wizolt a startup, I would expect to see a small number of people and a small web presence.
Still, I don’t accept invites willy-nilly.
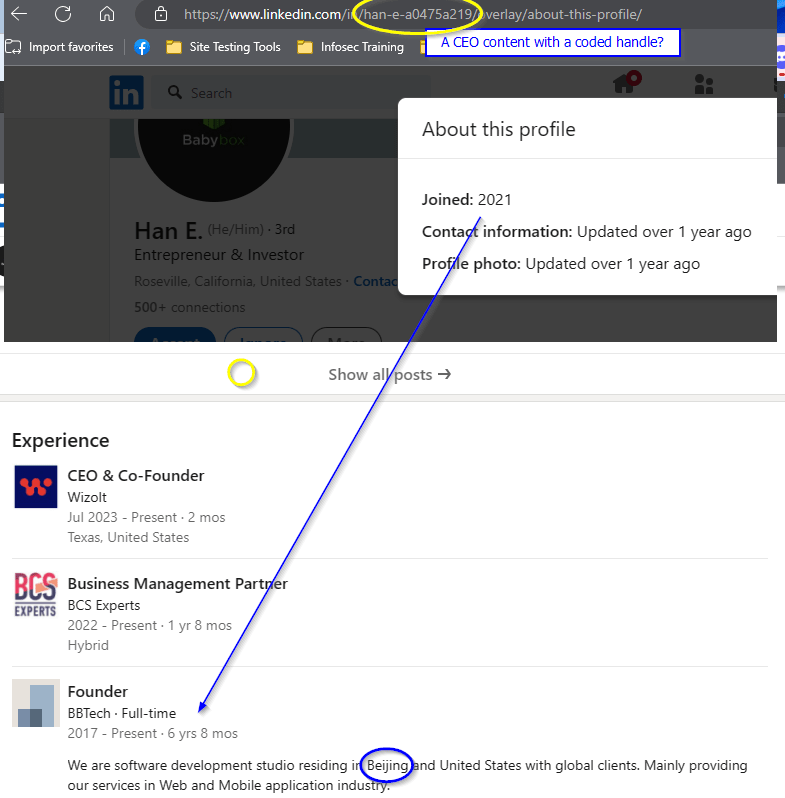
First thing is to check out the person’s profile. Several things struck me as odd about this. The first was the profile photo – clearly a product, but it didn’t match anything within the account’s profile.
Next, I stared at the last initial, combined with the LI account tag – “han-e-” plus a large hex number. Both of these show that our mystery Mister E doesn’t want us to look him up by last name.
The last bit that seemed suspicious to me is the profile age and his initial experience. The account is only a couple years old, but even so, this seems like a really thin experience track. “Founder”, “Partner”, “CEO”? People don’t just start up there. Plus that first experience lists the company as “residing in Beijing and the United States”.
The company page was pretty bare bones too. No cover photo – usually companies’ marketing departments have at least one promotional photo they’d like to highlight. But also, only one listed employee – our Mister E.
Thus, it’s time to go look at this company on the web. As a startup, I’m not expecting much, but my suspicions are raised further when the search engine returns multiple posts on the company by LinkedIn, and some of them are reposts by our new contact. Nothing from local company crawlers, no press releases, no BBB or D&B or anyone talking about them.
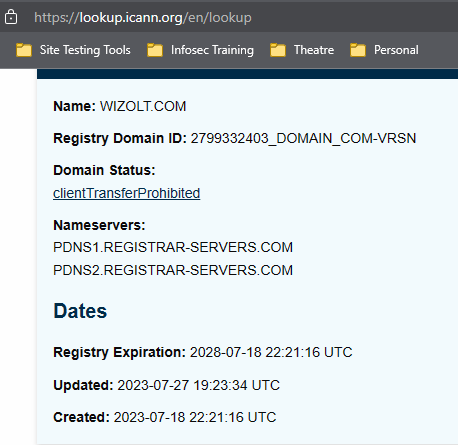


The next part of my search falls under the “experienced professional” category. An unknown website could be very dangerous. It could have a command that says, “When this page loads, also try to run this program.” So it’s best to approach it cautiously. First thing I did was look at how old the domain is, and whether anyone’s reported it for malware, etc. ICANN told me that it’s only a month old, and Virus Total said no one had reported it to the big anti-malware sites. A startup could be that recent, so I looked it up.
That’s where I found a couple other things. The About page listed the company as 2022 instead of 2023, but the real fun came when I scrolled further, to the list of employees. No CEO here. You have to scroll down to see each group of three, so folks who stop early wouldn’t notice that the same curly-haired person with glasses is two different people! Their VP of Operations is a “Wendy” who identifies as “she”, but clearly not the person in the image. Funnily enough, Wizolt already has an IT Manager – remember, that’s the position they sought me for – and he’s been with the company since 2013! Time travel’s apparently a thing. Finally, there’s the classic example of not understanding contractions by saying, “Your Next!”
Protecting Yourself
Hopefully, this shows you some methods to use to recognize the clues to a fake LinkedIn profile or company.
The best thing to do is take the time to look up what you can about an unknown person before you accept the invite. There’s also no harm in reaching out to mutual contacts or reviewing the caliber of the person’s public posts.

You must be logged in to post a comment.